Google Workspace
Frame supports Single Sign-On (SSO) with Google authentication through both OAuth2 and SAML2 integration options. The OAuth2 option is the easiest to setup and can be done in under a minute. The SAML2 option is also relatively quick and easy, but does require a few more steps.
Google Workspace OAuth2 SSO Integration
Google Workspace OAuth2 SSO integration is supported only when users access Frame via a supported web browser. Google Workspace OAuth2 is not supported by Frame App (due to Google Sign-In not supporting Chromium Embedded Framework).
Configuring Google Workspace OAuth2
- If you would like to enable Google Workspace OAuth2 integration with Frame, you will first need to following the procedure outlined in Google's guide to Control which third-party & internal apps access Google Workspace data.
- On the Google Admin Console home page, go to Security > API controls.
- Under App access control, click on MANAGE THIRD-PARTY APP ACCESS.
- Click on “Configure new app” drop down menu and select OAuth App Name Or Client ID.
- Search for the Client ID
884836301137-76l5epasioe5sb3qvsp31obn45qk6t5i.apps.googleusercontent.com. - Once you locate the Frame app in the search results, click Select.
- Check the checkbox for the Frame app with the Client ID
884836301137-76l5epasioe5sb3qvsp31obn45qk6t5i.apps.googleusercontent.comand then click SELECT. - For App access, specify that this Frame app is to be TRUSTED and click CONFIGURE.
Configuring Google OAuth2 in Frame
- Before Google OAuth2 can be added, the administrator must enable the Google toggle at a given level by navigating to the Admin Console. From there, navigate to the Customer or Organization page (depending on where you wish to add Google).
- Select Users from the left-hand menu.
- From there, navigate to the Authentication tab and enable the OAuth2 toggle. Click Save.
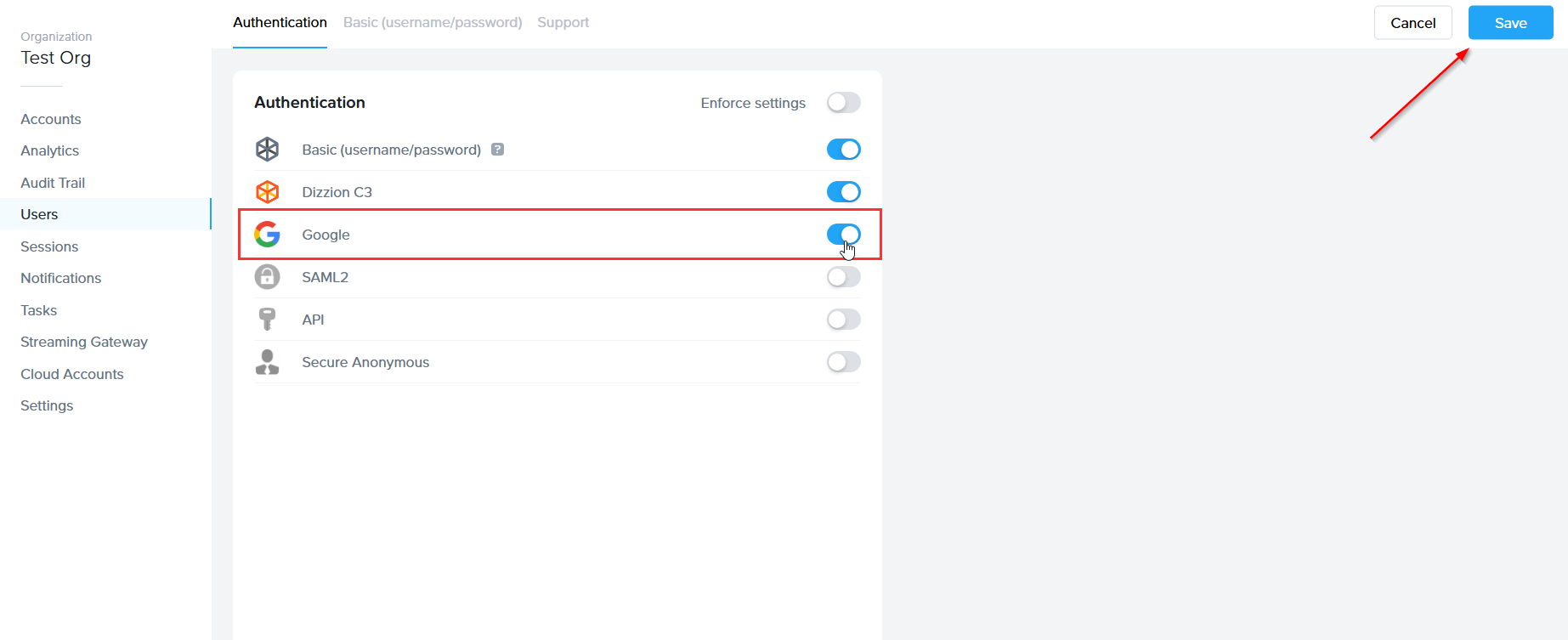
- Click on the newly created Google tab. From there, click Add.
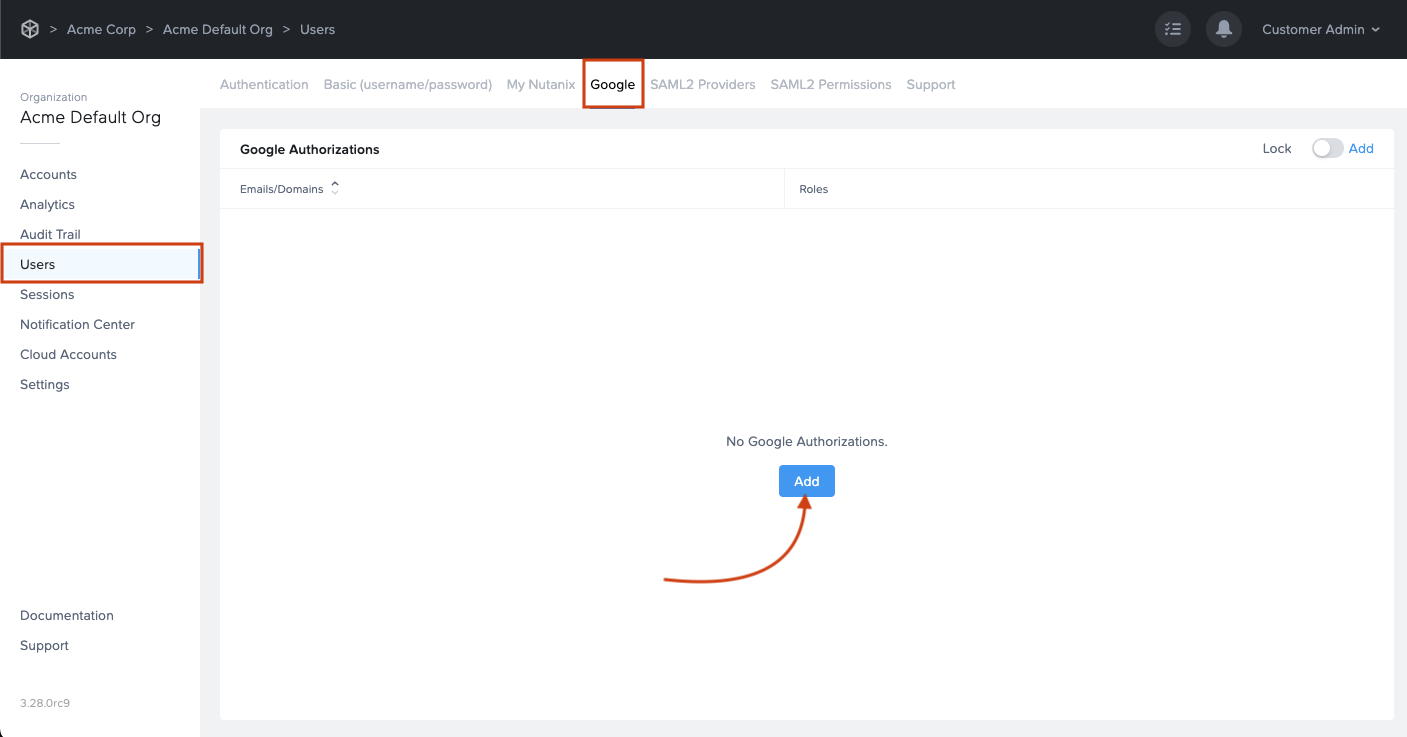
- The Add Google authorization dialog window will appear:
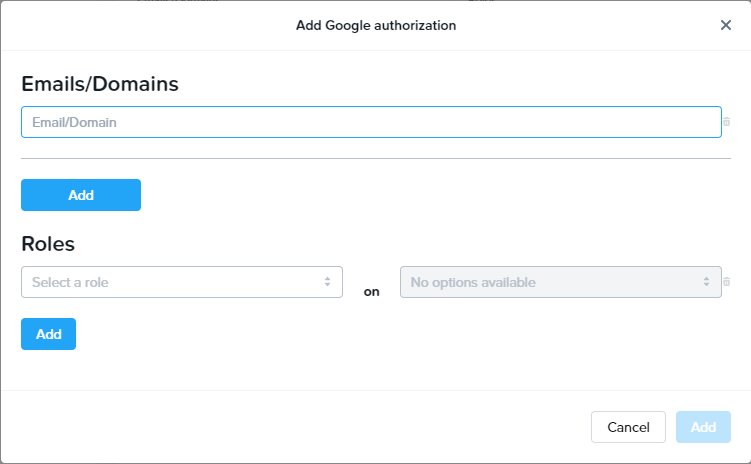
- From this window, you can specify individual email addresses or entire domains you wish to grant access to and their corresponding roles. For this example, we will give access to the domain mycompany.com. All users tied to this domain will be given “Launchpad User” access on the “Applications 2” Launchpad. Read more about permissions in the Manage User Permissions section of Frame documentation.
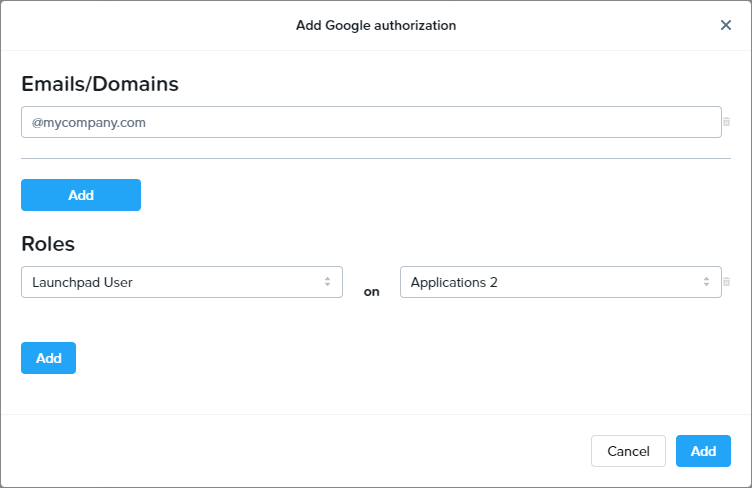
When specifying a Google Workspace domain, you must prefix the domain with the @ symbol, as shown above.
- Click Add when you have finished specifying your emails/domains and roles.
Signing in with Google Workspace via OAuth2
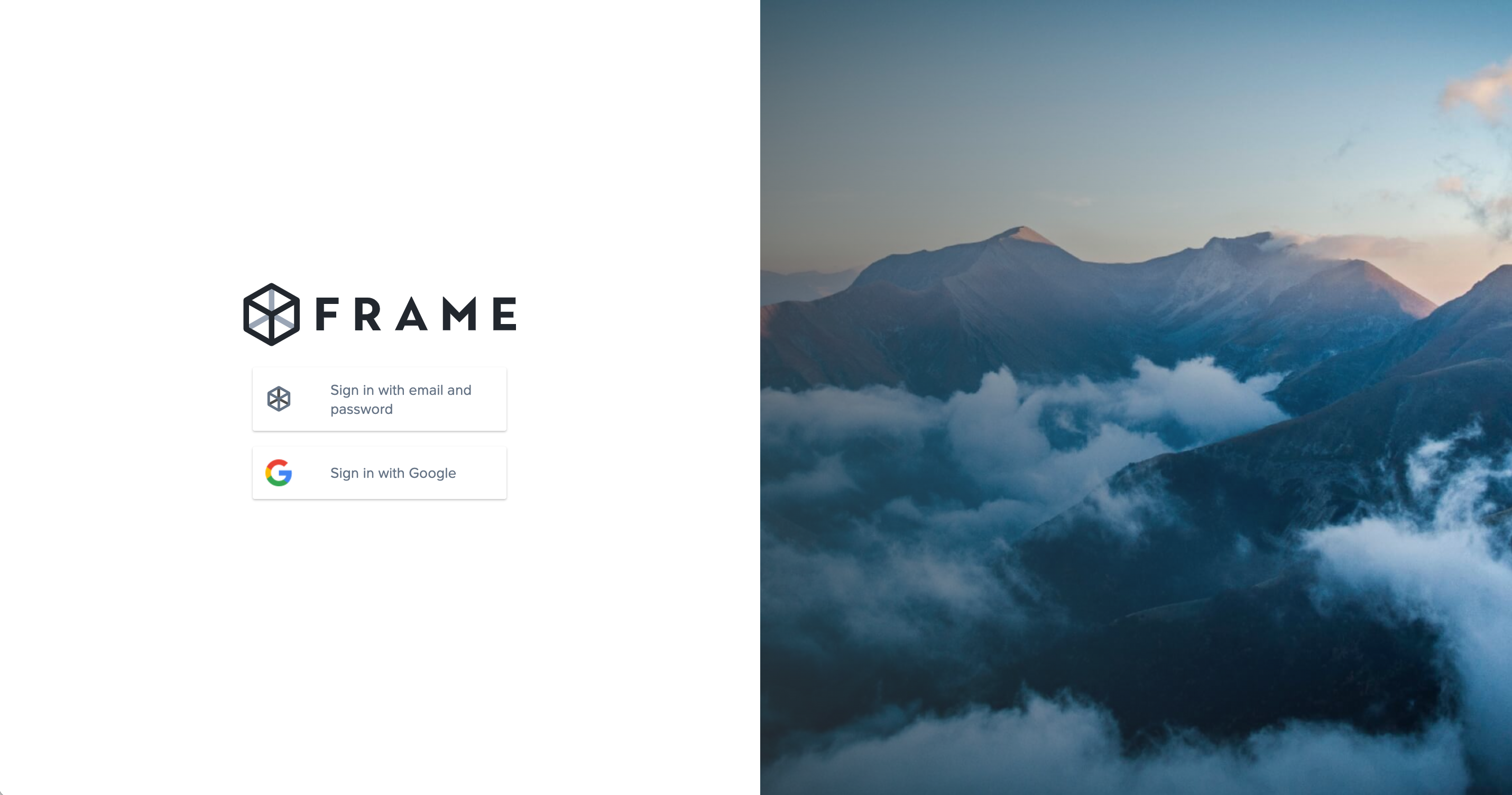
You can now instruct your users to select the Sign in with Google option when accessing their Frame login page and enter their Google credentials.
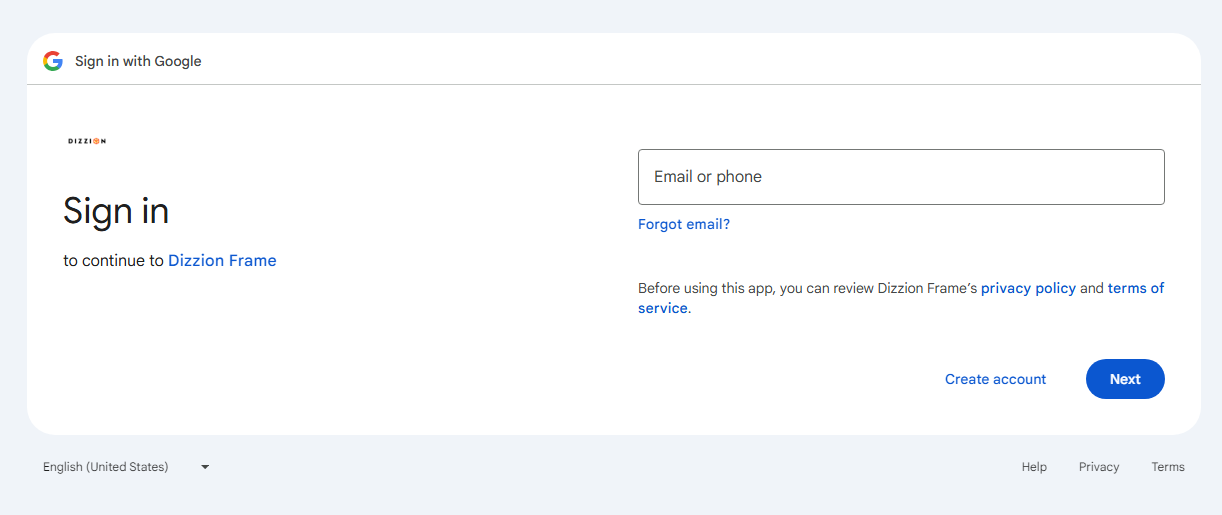
They will be prompted to allow Frame access to their Google Drive the first time they sign in.
That's it! Your users can now use Sign in with Google on your account via our OAuth2 integration option. If you prefer to set up your integration using SAML2, continue reading.
Google Workspace SAML2 Integration
Google Workspace SAML2 integration can only be set up by someone with a Super Admin role on a Google Workspace account. During this configuration process we will transition from the Google Workspace Admin console to the Frame console.
Getting Started
To begin, let's create a URL-friendly SAML2 Integration Name that we'll use in a few places throughout our setup. Continue below for help and examples that you can use in your SAML integration.
Integration Name examples for Google Workspace
Your SAML2 Integration Name is a case-sensitive, URL-friendly, unique, and descriptive value that represents the integration between your Google Workspace and Frame. This value can have only letters, numbers, and the dash symbol; no spaces or punctuation are allowed.
We recommend using something that includes descriptive information, such as your company and identity provider's names. This integration name is tied to your SAML2 endpoints on Frame and using descriptive names can be useful for debugging.
Optionally, fill out the information below to get a recommendation of what you could use.
Using the values copied from above and following the steps below, we'll create and gather these details to configure proper communication between ADFS and Frame.
Google Admin Console
-
Navigate and log in to to your Google Admin Console. Click on Apps and then Web and mobile apps.
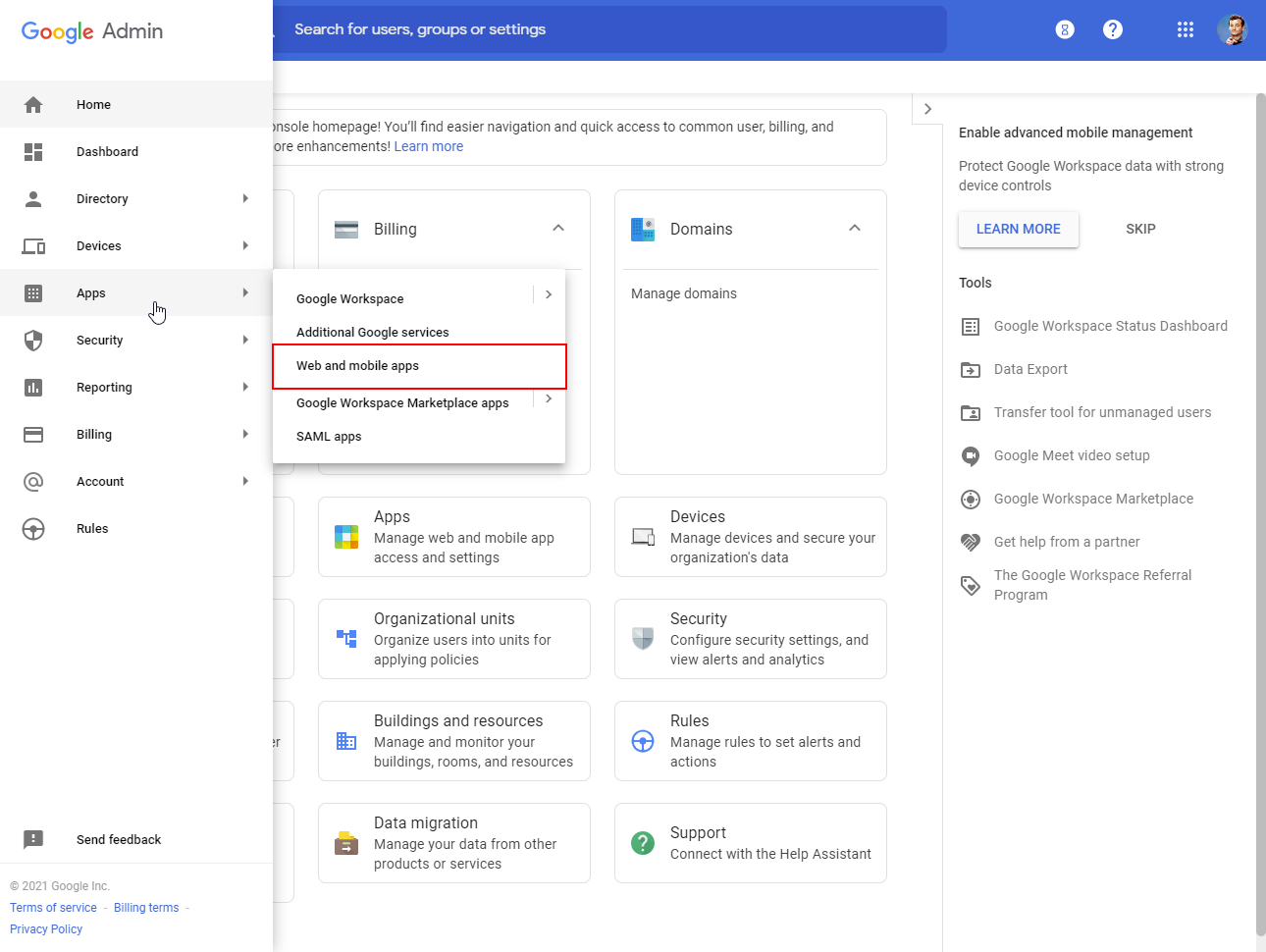
-
From the Apps Settings page, click Add App then Add custom SAML app from the drop-down.
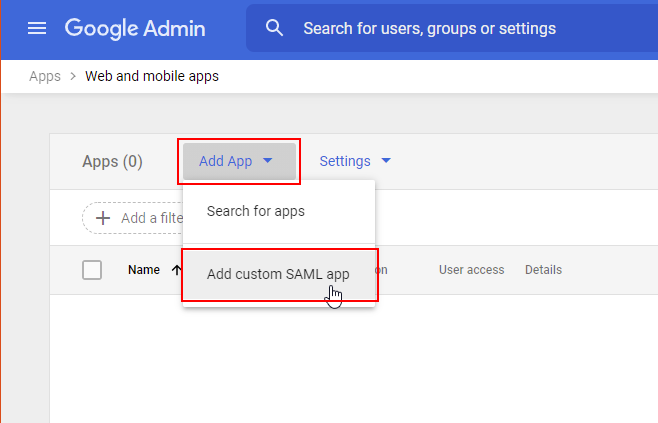
-
Enter "Frame” for the App name and upload our logo icon below (right-click, save).
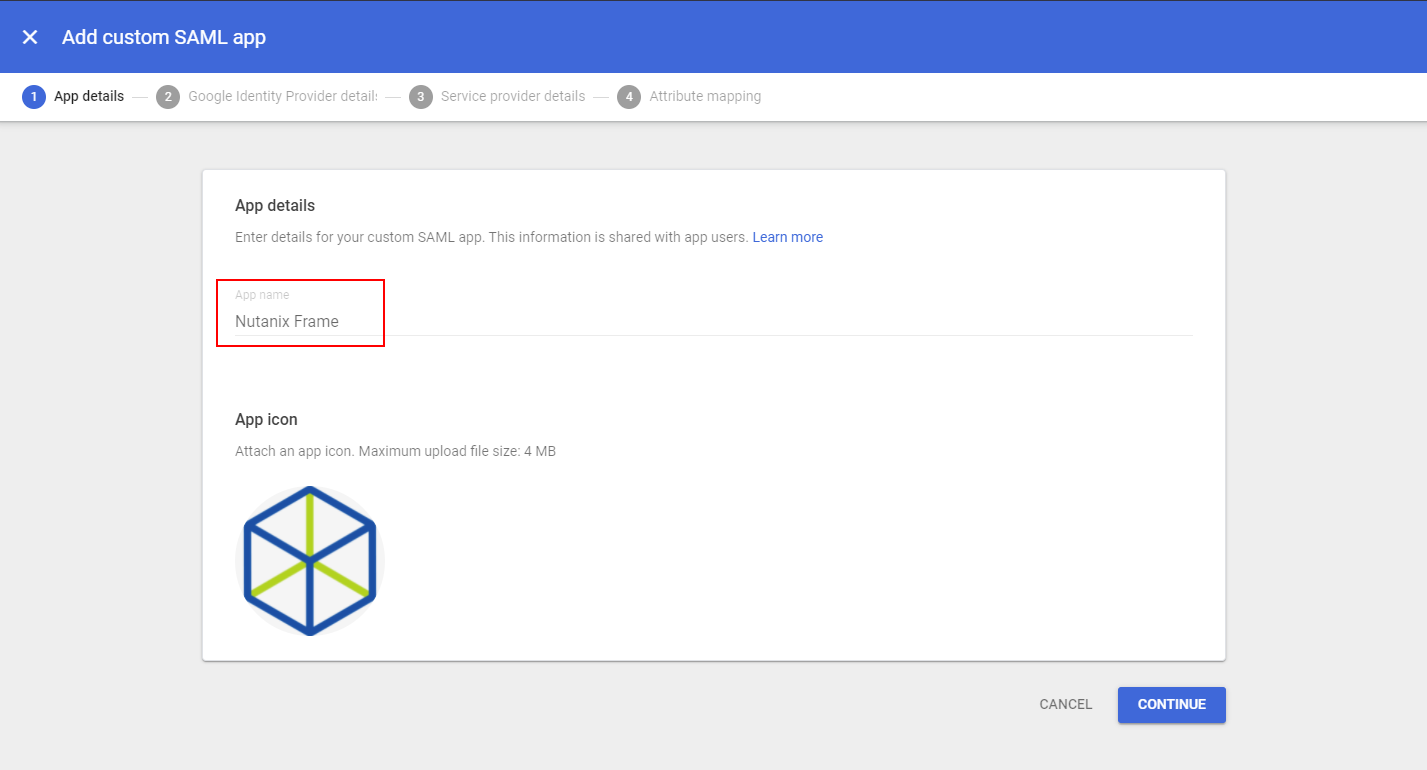

Frame Logo (right-click, save) Click Continue when ready.
-
Click the Download Metadata button. Save this somewhere accessible for a later step in the Frame Console; this metadata tells Frame how to communicate with Google on Frame's behalf.
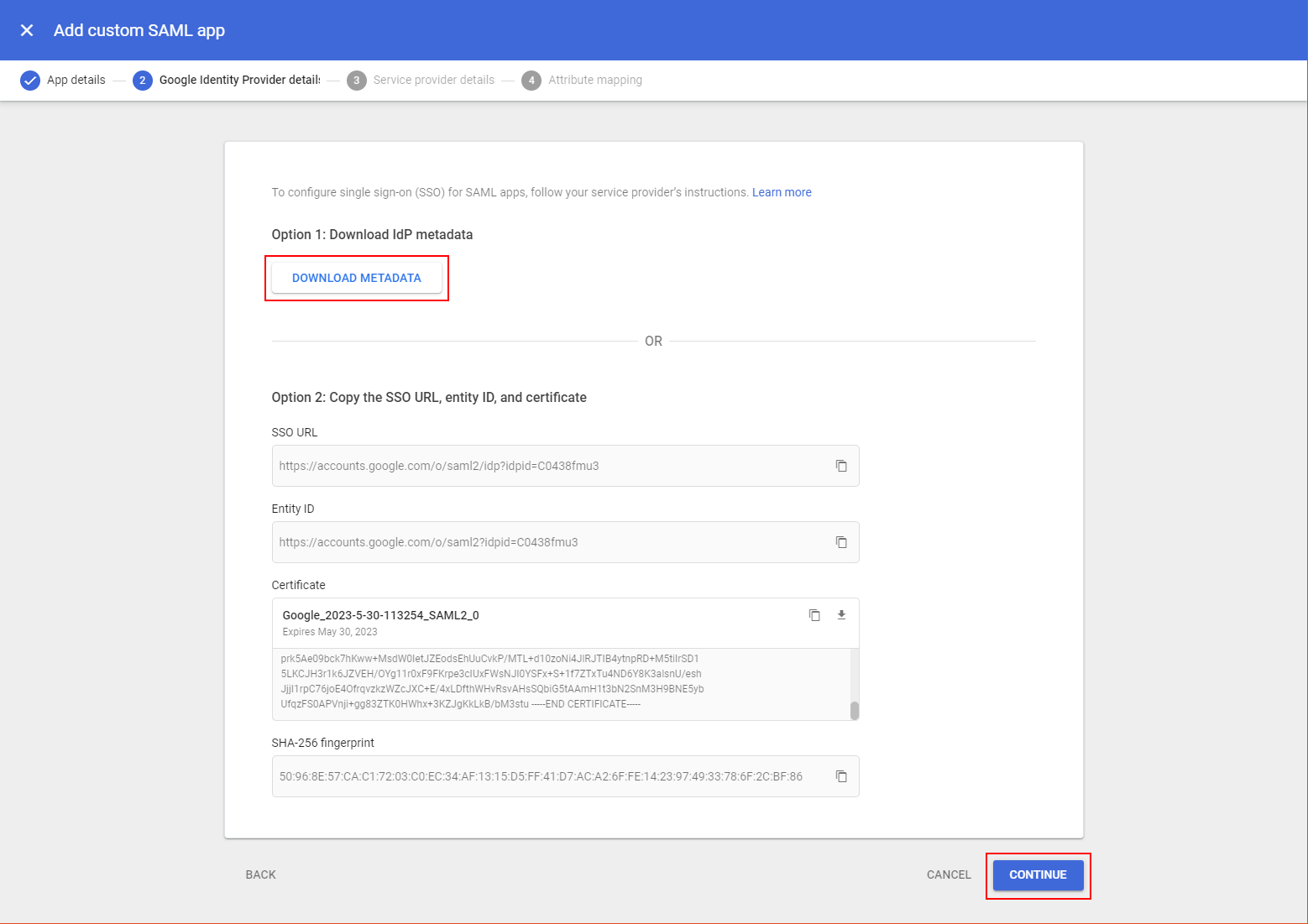
Click Continue when ready.
-
Next, we'll carefully enter values for ACS URL and Entity ID fields.
-
ACS (Assertion Consumer Service) URL: This is where Google will send assertions info (first name, last name, and email address) for authenticated users to Frame. Here, we'll enter the Frame ACS URL defined in the Getting Started section.
-
Entity ID: This field is also arbitrary and must be a URI, URN, or URL; this value is case-sensitive. Entity IDs are attached to event logs for Admin purposes and are required to match in both Google and Frame Console's settings to verify and identify each other via SAML2. For simplicity, we recommend using the Integration Name from the Getting Started section for this value. Copy the value you decide upon for use in later steps; Frame refers to the Entity ID in its SAML settings as “Application ID.”
-
-
Next, we have the Start URL.
The Start URL allows users to authenticate and navigate directly to Frame from Google's Workspace portal. This is often referred to as a “Identity Provider initiated login”. For most cases, the value for Start URL is simply a Launchpad or Account Dashboard URL to the account the user will have access to. If this field is left blank, your users can still log in to Frame with this Google App from the Frame Console's sign in page(s).
tipLeaving this blank may be desired if you have many Frame Accounts for your users to access or "land on".
-
Next, Ensure that the Name ID format field is set to PERSISTENT and the Name ID field is set to Basic Information > Primary email. Click Continue when ready.
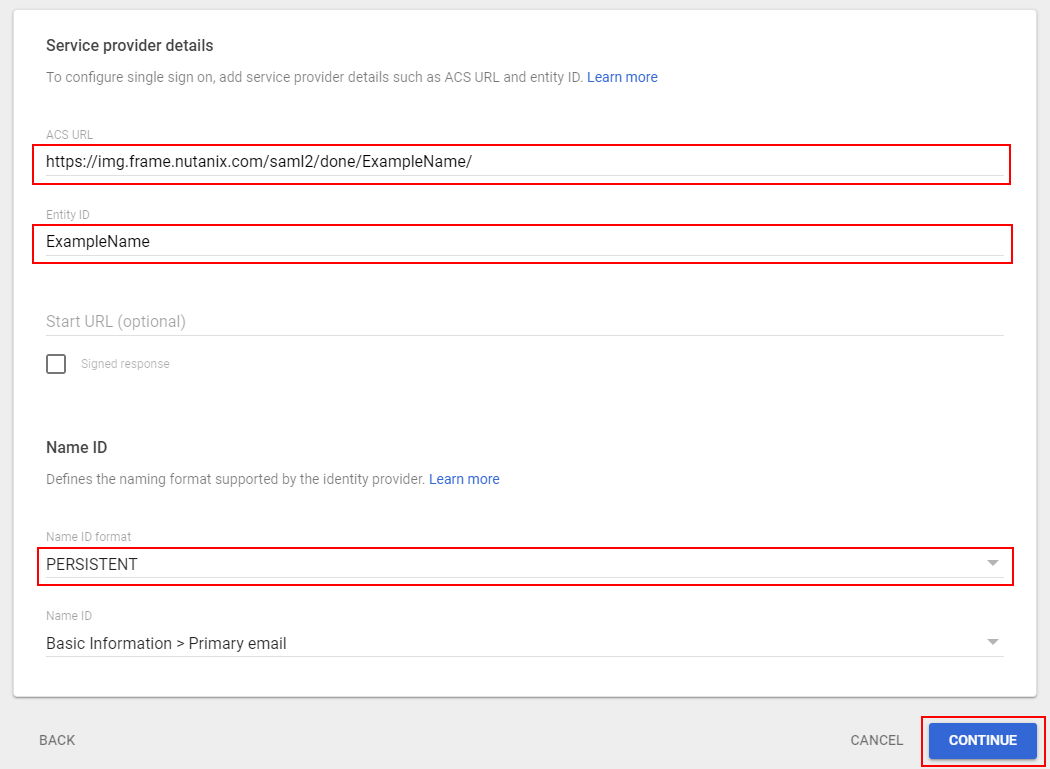
-
Here, we need to configure mappings between user fields from Google to recognizable terms that Frame is expecting to receive when users sign in. Fill it out exactly as pictured below:
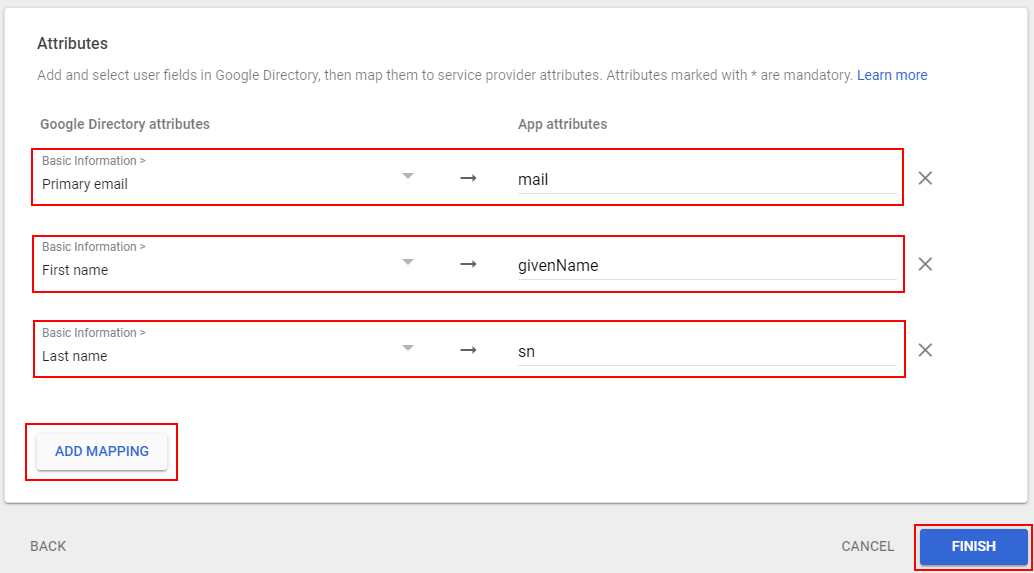
Click Finish when completed.
-
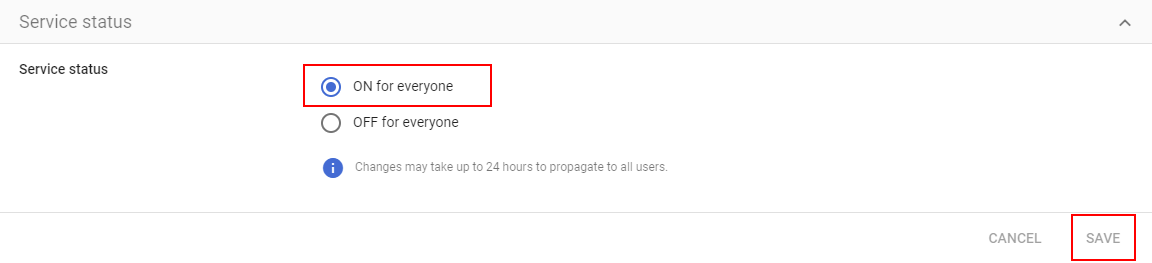
You'll now be brought to the main page of your new Custom App. The last thing we need to do is enable user access, as the default setting for new Custom Apps is OFF for everyone. To enable access, click in the User Access section at the top of the page.
Then, configure your user/group access and click SAVE. In our use-case, we wanted the service to be ON for everyone:
That's it for the Google Admin portion of the setup – we're half way there! By this point you should have the following items needed to setup Frame Console as the SAML2 Service Provider:
- Downloaded Metadata XML file
- SAML2 Integration Name
- Entity ID (later referenced as Application ID)
Configure SAML2 in Frame
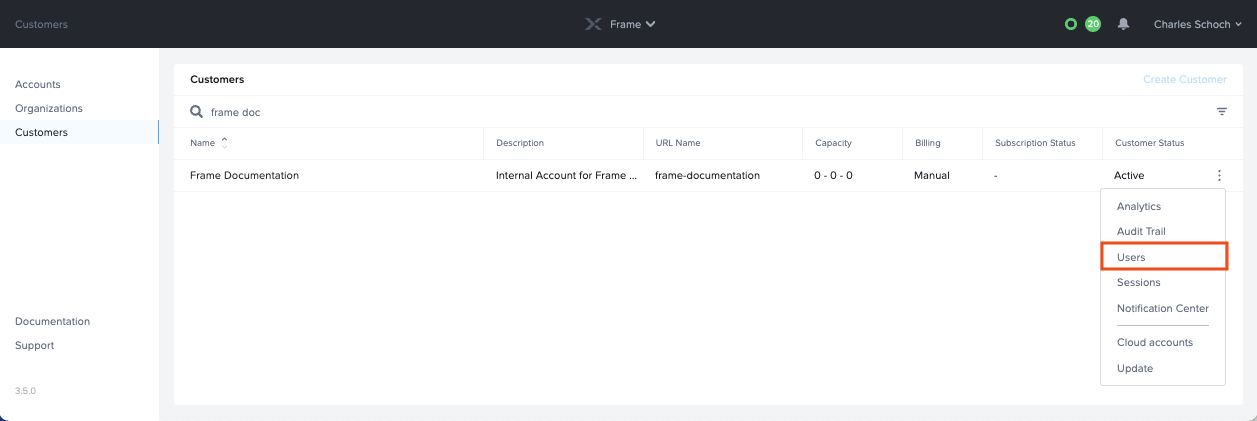
- Open up a new tab and navigate to your Frame account. A SAML2 authentication integration can be configured at any level (depending on administrative access) by navigating to the Admin page and clicking on the ellipsis listed next to the desired entity name. Select Users from the menu that appears. In our example, we're integrating with Google Workspace on the Customer scope/level.
-
Under Authentication, enable the SAML2 toggle and click Save in the upper right corner.
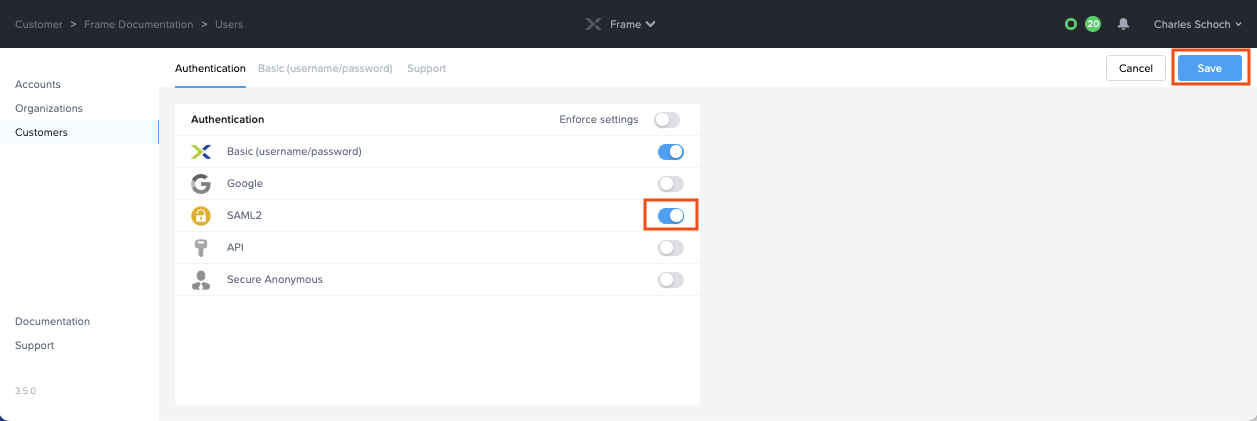
More options will appear next to the Authentication tab, click on the SAML2 Providers tab.
-
Click Add SAML2 Provider.
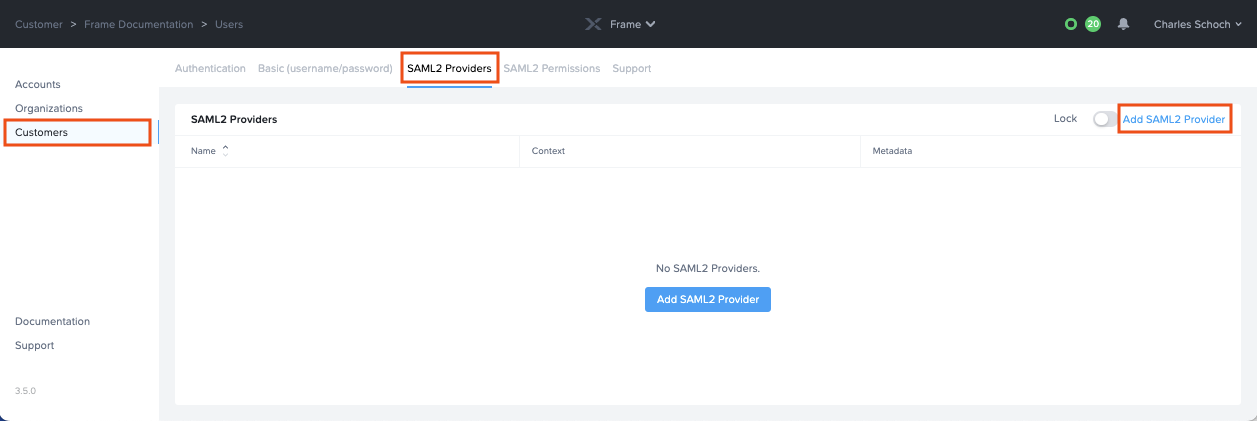
-
Next, we'll populate the fields to configure our SAML2 integration.
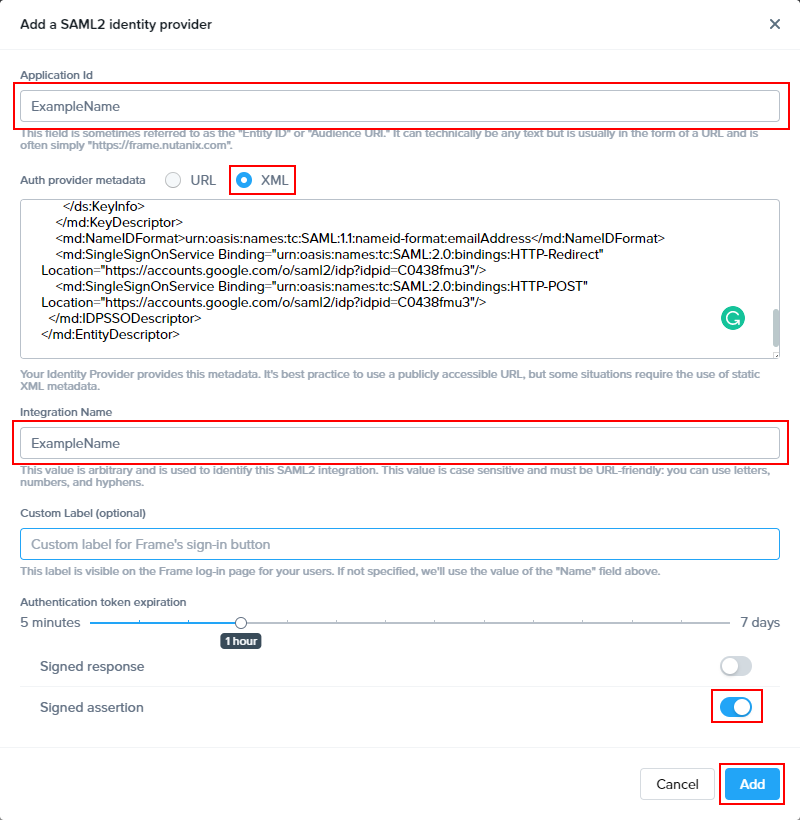
- Application ID: The value here needs to match the value set as the "Entity ID" from Step 5.
- Auth provider metadata: Click the “XML” option and paste the contents of the Metadata XML file from Step 4.
- Integration Name: Paste your chosen value of Integration Name from the Getting Started section.
- Custom Label: Optional. Allows Admins to customize Frame's Sign in page chiclets/buttons associated with this SAML2 integration.
- Authentication token expiration: Choose a token expiration duration that supports your end-user workflows and complies with your security policies.
- Enable “Signed assertion”
Lastly, confirm that everything is entered correctly and click Add.
Configuring SAML2 Permissions
Once the SAML2 Provider is successfully configured in the Nutanix Console, administrators will need to add authorization rules from the SAML2 Permissions tab listed to the right of the SAML2 Provider tab.
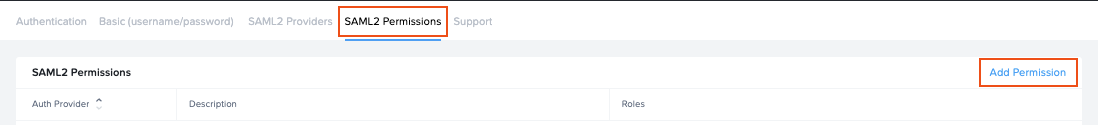
Add roles/permissions for your users by following our Roles and User Permissions with a SAML2 IdP guides.
Once you've configured permissions for your users, that's it! You're ready to test signing into Frame at your Entity URLs (Launchpad, Account Dashboard, etc.)!
Accessing Frame with Google Workspace
Your SAML integration will now appear to your users as a sign in button on your specific Frame Sign in Page.